Information and Communication Technology (ICT) has become an indispensable tool for development, and as a result, all countries, especially developing countries (e.g., Ghana), who paid the price for not taking part in the industrial revolution are putting in maximum effort not to miss out on the technological advancement and its attendant development, such as the growth of related industries and job opportunities. Ghanaians are gradually embracing ICT in their everyday lives, though the use of technology in Ghana is not as widespread as it is in other countries due to limited access to infrastructure and resources, a lack of education on technology and its uses, cultural reluctance to embrace digital tools, and illiteracy. The narrative is gradually changing as technology is been used in almost every sector of the economy, from manufacturing and industries, education, health, banking and finance, commerce, security, agriculture, creative arts and entertainment, the energy sector, etc. The political, social, and economic institutions, are all embracing technology.
In the education sector, almost all tertiary and pre-tertiary institutions have online portals for school application, admission, course registration, and results publications, as well as platforms for electronic learning and exams, which makes it incumbent for all students to frequently assess the platforms, thereby increasing technology usage among the populace. The health sector has equally witnessed the introduction of technological innovations like Hospital Management Systems, where patients’ data and medical histories are electronically stored. Software is used to coordinate the work of nurses, medical doctors, medical laboratory scientists, and pharmacists to provide healthcare. Technology is in use in the banking and finance sectors through electronic banking products and services such as Internet banking, mobile banking, and various Automated Teller Machine products. The collaboration between hardware, software, and telecommunication companies has made banks in Ghana introduce new ways for customers to access their account balances, transfer funds, pay bills, and buy goods and services without using cash, cheques or leaving home (Frei et al., 1998), as cited in Domeher, Frimpong, and Appiah (2014). Ghanaians are using technology in agriculture to improve yields through breeding domestic animals, crop cultivation, drone application, irrigation, etc. There is equally a huge technology application in the creative arts and entertainment industries in Ghana. For instance, instrumental and recording software for music production, digital music stores for marketing songs and artistic works, and apps like Facebook, Tik-Tok, Instagram, Telegram, Twitter, YouTube, etc. for content creation and music promotion. These have greatly contributed to the increased percentage of internet penetration in Ghana as these apps are monetized, hence the activities on them earn the users income.
Ghana is the first country in sub-Saharan Africa to have full internet connectivity (Sulzberger, 2001, cited in Zachary, 2014). The many digital devices owned by Ghanaians indicate the love for the internet among the populace. As of the third quarter of 2019, Ghana counted 16.7 million unique mobile subscribers, 15.1 million smartphone devices, and 10.7 million mobile internet users in the country (as of Q3 2019) (Omondi, 2020). The world is now a global village; hence, the use of digital devices has become a necessity and not a luxury. Ghanaians use these digital devices to apply for jobs, purchase goods, study, sell or market their products and services, and entertain themselves in cyberspace. Ghana has the highest mobile penetration in West Africa and already outperforms many of its regional peers. By the end of 2019, mobile adoption stood at 55 percent, higher than the regional average, which was 44.8 percent. This means a large number of people can be served through digital services, positively impacting the growth of the digital economy (Omondi, 2020). As of January 2022, Ghana registered approximately 45 million mobile connections, up from 41.69 million in the same month of the previous year. The number of mobile connections corresponds to 140 percent of Ghana’s total population, as one person can use multiple networks at the same time (Sasu, 2022). The significant increase in technological usage in Ghana can be attributed to the liberalization of the ICT sector, which has contributed to 16.99 million internet users with an internet penetration rate of 53 percent as of January 2022 (Kemp, 2022). The advancement in technological devices and the internet has created a different world where one does not require a visa before entry; hence, all manner of behaviors from the physical world have been exported to the newly created world.
Ideally, the invention of computers and the internet were to make life and work easier, increase productivity, and help improve and develop businesses and organizations until the emergence of cybercrime, which has threatened the very reasons computers and the internet were invented. This has also compounded the already existing criminal activities bedevilling the country as well as the security services. The information society is not only affecting the way people interact, but it is also requiring traditional organizational structures to be more flexible, participatory, and decentralized. For example, a lot of companies have adopted ERP (Enterprise Resource Planning), a software that helps companies automate and manage their core business processes, including accounting and resource management. Digital devices make use of cyberspace, and just like in every environment, as technology advances, it gives room for criminals to identify loopholes to operate in or take advantage of cyberspace, hence Cybercrime.
THE CYBERCRIME LANDSCAPE
Cybercrime is a general term for any illegal activity that uses a computer as its primary means of commission (Halder & Aishankar, 2011; cited in Barfi, Nyagorme, & Yeboah, 2018). The issue of cybercrime is more than just the use of the internet or computers to perpetrate criminal activities. According to the United States Department of Justice (DOJ) cited in Brush, Rosencrance, and Cobb (2021), cybercrime can be categorized into crimes in which the computing device is the target, such as gaining network access; crimes in which the computer is used as a weapon, for instance, to launch a denial-of-service (DoS) attack; and crimes in which the computer is used as an accessory to a crime, for example, using a computer to store illegally obtained data.
The integrity of networks, devices, and processes that are connected to the internet or within the online space can be compromised by groups or individuals called cyber threat actors. With malicious intent, they aim to exploit weaknesses in an information system or exploit its operators to gain unauthorized access to or otherwise affect victims’ data, devices, systems, and networks, including the authenticity of the information that flows to and from them. The globalized nature of the Internet allows threat actors to be physically located anywhere in the world and still affect or remotely attack the security of information systems in any country (Canadian Centre for Cyber Security, 2022).
Cyber threat actors can be categorized by their motivations, actions, and, to a degree, sophistication. Threat actors value access to devices and networks for different reasons, such as siphoning processing power, exfiltrating or manipulating information, degrading the network’s performance, and extorting from the owner. It is believed that cyber threat actors are not equal in terms of capability and sophistication. They have a range of resources, training, and support for their activities. Cyber threat actors may operate on their own or as part of a larger organization (i.e., a nation-state intelligence program or organized crime group). For instance, in 2022, an 18-year-old teenager hacked several Uber databases. The hacker is reported to have provided screenshots of internal Uber systems to demonstrate his access. His motivation stems from Uber’s weak security and poor remuneration for drivers, as stated by the hacker. Uber, on the other hand, is of the view that the act was motivated by fame, not money (McMillan, 2022). Whichever way the motivation may have emerged, the problem remains that Uber suffered data breaches as a result of the attack.
On October 28, 2019, Georgia got hit by a massive cyberattack that knocked out up to 15,000 state, private, and media websites, as well as the national television station. Website home pages were replaced with an image of former Georgian President Mikheil Saakashvili and the caption ‘I’ll be back’. Court websites containing case materials and personal data were equally attacked (Gotev, 2020). The cyberattack on Georgia appears to be motivated by more geopolitical factors. The attack is suspected to have been perpetrated by the Main Center for Special Technologies (GTsST, or “Unit 74455”) of the Russian General Staff Main Intelligence Directorate (GRU), namely, the Russian military intelligence service. This is according to the Georgian government, the United Kingdom, the United States, the European Union, and many other states in a series of generally coordinated statements (Roguski, 2020).
The Canadian Centre for Cyber Security (2022) outlined the following cyber threat actors and the motivation for their actions:
Nation-States/Espionage: State-sponsored cyber threat actors operating on behalf of nation-states primarily use cyber threat activity to advance their geopolitical objectives. They are frequently the most sophisticated threat actors, with dedicated resources and personnel, extensive planning, and coordination. Nation-states without developed cyber programs can use commercial cyber tools and the growing global pool of talent to enable sophisticated cyber threat activity. Some nation-states also have operational relationships with private sector entities and organized criminals.
The activities of state-sponsored cyber threat actors may include espionage against governments, organizations, and individuals; prepositioning on or disrupting critical systems; influencing and shaping public discourse; or building networks of compromised devices to enable further cyber-attacks. State-sponsored cyber threat actors may also pursue financially motivated threat activities.
Cybercriminals are primarily financially motivated and vary widely in sophistication. Organized crime groups often have planning and support functions in addition to specialized technical capabilities that can affect a large number of victims. Illegal online markets for cyber tools and services have made cybercrime more accessible and allowed cybercriminals to conduct more complex and enlightened campaigns.
Hacktivists carry out ideologically motivated cyber threat activity and are generally less sophisticated than state-sponsored cyber threat actors or organized cyber criminals. These actors, along with terrorist groups and thrill-seekers, often rely on widely available tools that require little technical skill to deploy. Their actions often have no lasting effect on their targets beyond reputation, however, at times, these actors have been able to inflict physical and financial damage on their targets.
Insider threats are individuals working within their organization who are particularly dangerous because of their access to internal networks that are protected by security perimeters. Insider threats are often disgruntled employees and may be associated with any of the other types of threat actors listed. They typically steal proprietary information for personal, financial, or ideological reasons.
Thrill-seekers are individuals who illegally access computer systems for the challenge of it. They are threat actors who attack computer systems or networks for personal enjoyment. Whether they want to see how much data and sensitive information they can steal or are interested in how specific networks and computer systems operate, thrill-seekers may not necessarily intend to do much harm to their targets. However, they can interfere with computer systems and networks or exploit vulnerabilities for more cyberattacks in the future.
CYBER ATTACK TECHNIQUES
A cyberattack is when a third party gains unauthorized access to a computer system or network. Once the attacker or hacker gains access to or control of a system, there may be data loss, or manipulation, resulting in financial loss or reputational damage to the organization. Many forms of cybercrime methods or techniques are usually adopted by cybercriminals to execute attacks on business-critical systems. Among these are:
Malware Attack: Malware is malicious software designed to commit a crime or harm computer systems. Examples of malware used by attackers include worms, ransomware, adware, trojans, and spyware. The trojan virus disguises itself as legitimate software. Ransomware blocks access to the network’s key components, whereas Spyware is software that steals all your confidential data without your knowledge. Adware is software that displays advertising content, such as banners, on a user’s screen. Other malware include botnets, Rookit, etc. To avoid malware attacks, one must use strong antivirus and firewalls and also avoid clicking on suspicious links.
Social engineering is the use of deception to gain vital information or manipulate a system. A common example is a Phishing attack, where attackers use fake emails, websites, or messages to trick victims into revealing sensitive information, such as passwords or credit card details. It allows one to gain access to confidential information and account credentials.
Password Attack: This is a form of attack where attackers try to guess or crack passwords to gain access to a system or network. They may use brute-force attacks, dictionary attacks, or other techniques to crack weak passwords. This can be prevented by using strong alphanumeric passwords with special characters, avoiding the same password for multiple websites or accounts, and not leaving password hints in the open.
Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) attacks: these attacks are malicious attempts to disrupt the normal traffic of a network. This is done by overloading a network with more packets than it can handle to exhaust its resources and bandwidth, thereby causing it to shut down.
Man-in-the-middle (MitM) attacks In a MitM attack, also known as an eavesdropping attack, an attacker intercepts communications between two parties to steal data, modify messages, or impersonate one of the parties. To prevent this, one must use encryption on devices and refrain from using public Wi-Fi networks.
SQL injection attacks A Structured Query Language (SQL) injection attack occurs on a database-driven website when the hacker manipulates a standard SQL query. It is carried out by injecting malicious code into a vulnerable website search box, thereby making the server reveal crucial information. SQL injection attacks exploit vulnerabilities in web applications to gain unauthorized access to databases and steal or modify data. Database designers must use an Intrusion detection system to detect unauthorized access to a network.
Zero-day attacks: These happen after an announcement of a network vulnerability; there is no solution for the vulnerability in most cases. However, when users are notified of the vulnerability, the news also reaches the attackers. Zero-day attacks exploit previously unknown vulnerabilities in software or systems, giving attackers a significant advantage. Having an incident response plan and a well-communicated patch management process could prevent these kinds of attacks.
PREDOMINANT CYBER CRIMES
Cybercrime is a criminal activity punishable by law; hence, no attempt should be made to justify or legitimize its illegality. It has become one of the crimes bedevilling the Ghana Police Service and the country in recent times. The police have observed with keen attention that many Ghanaians perceive cybercrime to mean only cyber fraud. This perception has created a layer of obstacles to addressing cybercrime, hence the urgent need to expose the various forms of cybercrime to the citizenry. Below are some of the most common cybercrimes in recent times:
Figure 1: Common Cybercrimes
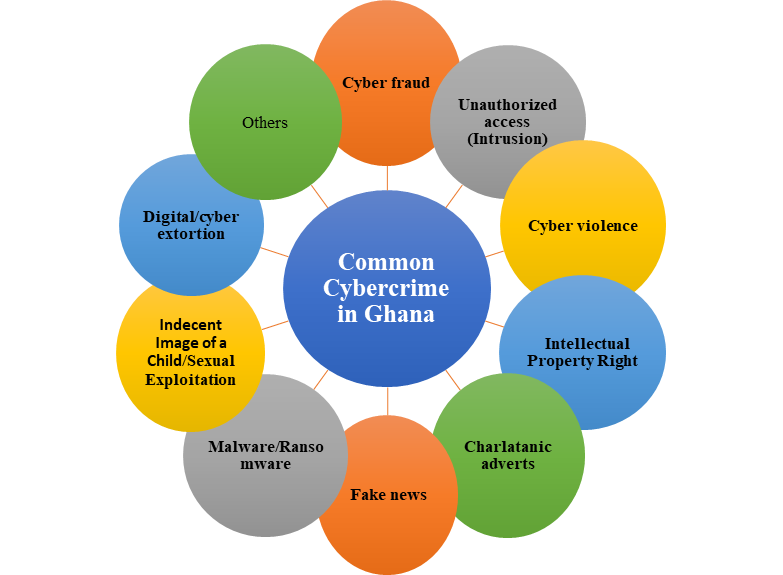
Cyber fraud is the use of the internet to get money, food, services, etc. from people illegally by tricking them (otherwise known as ‘419’). This is believed to constitute about 45% of all cybercrime cases in Ghana, according to the Cybercrime Unit of the Police Service.
Unauthorized Access (Intrusion): It occurs when criminals attack the digital and networking systems of their targets without authorization, purposely to steal valuable network resources, gather information on users, steal data and documents, disrupt data-related activity, or cause damage to or corrupt systems. For example, hacking and data breaches are forms of intrusion. For instance, the hacking of Ghanaian government websites in the early part of 2015 highlights some of the attacks targeted at government technology infrastructure. In 2016, the Electoral Commission of Ghana had its website hacked during the transmission of election results. In April 2017, several websites of media houses were targeted through Distributed Denial of Service (DDoS) attacks. In 2022, the Electricity Company of Ghana (ECG) had its prepaid vending system hacked for weeks, during which customers were unable to purchase prepaid. Website defacement and unauthorized modification are all forms of unauthorized access.
Cyberviolence: This includes stalking and bullying. Cyberstalking is the use of the internet or other electronic means to stalk or harass an individual, group, or organization. Cyberbullying is when one or more individuals use digital technologies to intentionally and repeatedly harass and cause harm to another person. This is a practice that is very common in Ghana, mainly due to the lack of effective implementation of available laws. For instance, in 2021, some media personalities by the names of, Nana Aba Anamoah, Serwaa Amihere, and Bridget Otoo cyberbullied Albert Hyde during an audition for a television program in which the victim participated. To many, what transpired was just an attempt to give the victim a taste of his own medicine, as he is known for cyberbullying celebrities and media personalities on Twitter and Facebook.
Intellectual Property Rights (Software Piracy): the illegal copying, distributing, sharing, selling, or use of software, whether intentional or not.
Charlatanic ads: the publication in any journal or newspaper of any advertisement or notice relating to fortune-telling, palmistry, astrology, or the use of any subtle craft, means, or device sought to deceive or likely to deceive any member of the public. The Police Service has consistently been reminding the Ghanaian people that charlatanic advertisements are criminal and punishable by law. The Police have arrested several people, and some were prosecuted, including the founder of Heaven Way Church, Patricia Oduro Koranteng, aka Nana Agradaa, who was arrested for that offence.
Fake news to endanger life and property—news or stories created to deliberately misinform or deceive readers. For instance, in early January 2023, an audiotape was circulated where the narrator gave a vivid story of how some police officers implanted cocaine and weed in his car and turned around to arrest him. The police invited and later arrested the said person to aid them in the investigation, only to find out that the whole story was fabricated. In Ghana, the spreading of fake news is against Section 76 of the Electronic Communication Act 2008 (Act 775).
Indecent Image of a Child/Sexual Exploitation: any visual depiction of sexually explicit conduct involving a child, which includes a photograph, video, digital, or computer-generated image indistinguishable from an actual child, and an image created, adapted, or modified but appearing to depict a child. In Ghana, a lot of people have been prosecuted for child pornography. In the recent past, a social media figure called Rosemond Brown, aka Akuapem Poloo was arrested and charged for posting her nude picture with her half-naked son on the internet.
Digital or cyber extortion is the act of coercing or forcing an individual or company to pay in exchange for gaining back access to stolen cyber assets. When a cyber attacker demands money or something else in return for stopping the attack or returning access to systems or data. This includes Sextortion, where one threatens to distribute or circulate private and sensitive material about someone if the person does not provide him or her with images of sexual nature, sexual favours, or money. For example, the recent publication of a sex tape involving a popular television host, Serwaa Amihere and one Henry Fitz, which is alleged to have been released due to the inability of the former to pay the amount demanded by the blackmailers. The Cybercrime Unit of the Ghana Police reported a record of ten (10) sexual extortion cases in less than a month in January 2019. In 2022, a phone repairer in Ghana was sentenced to 14 years imprisonment for sexual extortion and non-consensual sharing of intimate images of a Lebanese woman.
Others include cyberlaundering, cyberterrorism, Crypto-jacking, Espionage, theft, unauthorized modification, identity theft, etc.
COMMON CYBER FRAUD IN GHANA
The Ghana Police Service is working assiduously to curb the incidence of cyber fraud, as reports by the Cybercrime Unit indicate that cyber fraud cases constitute up to 45% of all cybercrime cases in Ghana. Cyber fraud has replaced or becomes the modern-day confident tricksters who used to approach people physically and manipulate them into parting with money or goods, otherwise known as ‘419’. According to INTERPOL in Ghana, most of the cybercrime cases they receive from their counterparts in various countries are fraud.
Figure 2: Common Cyber fraud in Ghana
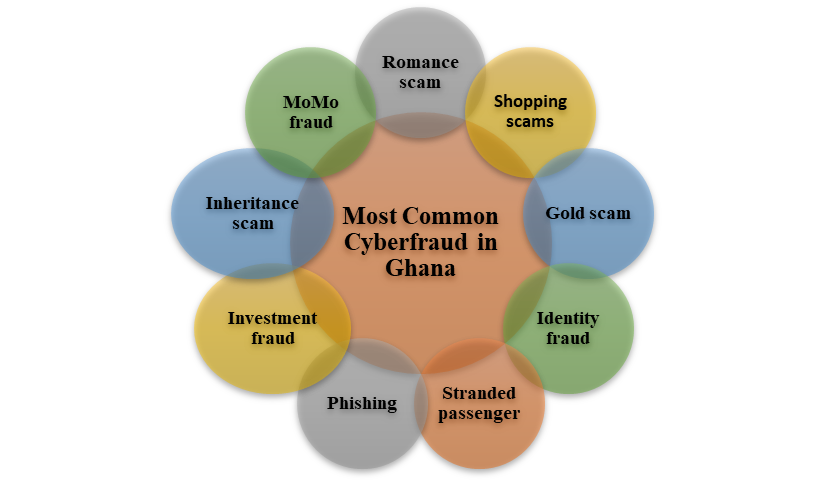
The most prevalent form of cyber fraud in Ghana includes but is not limited to;
A romance scam occurs when a criminal adopts a fake online identity to gain a victim’s affection and trust. The scammer then uses the illusion of a romantic or close relationship to manipulate and/or steal from the victim by way of convincing victims to send nude photos of themselves, which are later used to demand money, with threats to publish photos if demands are not met.
Shopping scams: this type of cyber fraud has become more prevalent as electronic commerce has become the order of the day. It occurs when people shop online and make payments through electronic means with the expectation of the product being delivered to them, but it turns out to be a deception.
Gold scam: this occurs when gold scammers present fake photos and videos of gold available for sale. Some of these eventually turn out to be gold-plated tungsten. Using the fake pictures and videos, the gold scammers then convince victims to provide huge amounts of money to transport the gold from the mining sites or specific locations to Accra for the said sale transaction. Once the scammers received the money for the supposed transportation of the gold, various excuses were given as reasons for their failure to deliver the gold to Accra. The scammers use these excuses to claim more money to facilitate the delivery of the gold, which eventually turns out to be a deception. In addition to this tactic, scammers also export some grams or a kilo of gold, purposely to win the confidence and trust of their victims and also to prove their ostensible capacity to supply larger quantities. Once the victim’s trust is won, demands for huge sums of money are made, after which the fraudsters disappear, leaving their victims frustrated.
Identity fraud occurs when someone uses another person’s personal identifying information, like their name, identification number, or credit card number, without their permission, to commit fraud or other crimes.
Stranded passenger: Stranded passenger is when cyber fraudsters take control of your email and send impersonated messages purporting to be coming from known contacts of their targeted victims. They send convincing messages, mostly indicating that they are stranded in other countries and need urgent financial support. Communication ends the moment the money is received.
Investment fraud: this involves the use of deceptive practices to entice people into making unreasonable decisions in investing in areas such as gold, cocoa, real estate, sales, and many more, which consequently result in huge investment losses. The issues regarding investment fraud have often been at the door of the Ghana Police Service. Investors are often presented with a very high dividend and an investment with no or little risk involved.
Inheritance scam: these scams offer you the false promise of an inheritance to trick you into parting with your money or sharing your bank or credit card details. A scammer may contact you out of the blue to tell you that you can claim a large inheritance from a distant relative or wealthy benefactor. In the process, they request that you send them some money to enable them to secure the said inheritance, which turns out to be false.
MoMo fraud involves fraudulent acts perpetrated against mobile money (MoMo) users through the use of deceit to get unsuspecting victims to part with money. For instance, the Raffle Scheme (one receives a call that he or she has won a raffle, and to claim the prize, some amount of money would have to be paid); the long service award (one receives a call that he or she has been a long serving customer and is eligible for an award. The fraudsters then request money as part of requirements for the award); another scheme is the False SMS (a false SMS is sent to your number claiming that money was mistakenly sent to you and that you should send it back). If an unsuspecting victim fails to crosscheck his or her account balance, he or she may end up sending their own money to the fraudsters), Sick Child Scheme: (the fraudsters manage to gather intelligence on their target victim, call with the information that his or her child is sick and has been admitted to the hospital. They would then request some amount of money urgently needed to settle some bills of the victim’s child otherwise the hospital staff would not attend to the child).
There is also Police Arrest Scheme, Romance Scheme (mostly carried out on social media), Transaction Reversal Scheme, and Spiritual Schemes (someone calls claiming that he has been asked to kill you through spiritual means but then he wants to spare your life so send him some money as compensation) and Fraudulent SIM Swap Scheme (the fraudsters can convince the Tele-Communications Company (TelCos) to change someone’s SIM and re-register it under their details so that they can have control and use it).
Figure 3: Cybercrime cases reported in Ghana from 2016-2022.
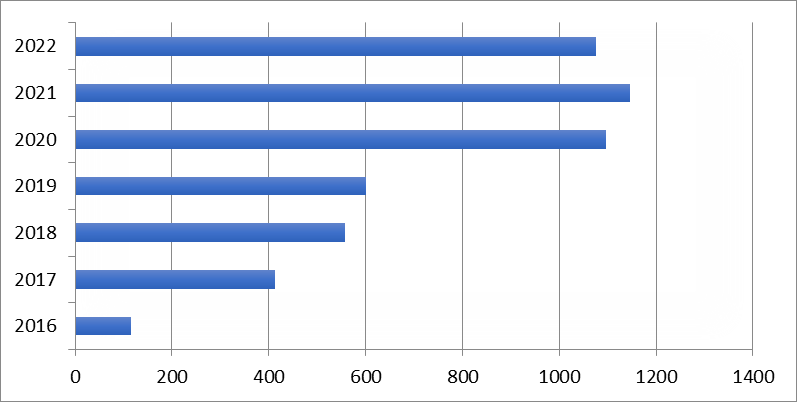
Source: The Cybercrime Unit of the Criminal Investigation Department, Ghana Police Service.
Figure 3 indicates cybercrime cases reported over the past seven 7 years. The number of cases reported to the Ghana Police Service as indicated by the Cybercrime Unit shows 116, 412, 558, 600, 1097, 1147, and 1077 cases of cybercrime in the years 2016, 2017, 2018, 2019, 2020, 2021, and 2022 respectively. These figures have prompted the Police Service to intensify the education and awareness creation among the citizenry to help curb the menace. The numbers show a trajectory of increase in the number of cases from 2016-2021 until 2022 where a slight decrease was witnessed. It can equally be argued that the various interventions of the Ghana Police Service are beginning to pay off. For instance, the Ghana Police Service through the Cyber Crime Unit over the years has been investigating and prosecuting cybercriminals; collecting data and undertaking forensic analysis; cyber intelligence collection, analysis, and dissemination; assessing and analyzing cybercrime phenomena; and surveilling and monitoring the cyberspace which to a larger extent appeared to have yielded results manifesting in a decrease in the number of cybercrime cases reported in 2022. The Police Service as part of their intervention to secure cyberspace has arrested and prosecuted some people who are perpetrators of this crime.
The increase in cybercrime cases reported signifies the acknowledgement of the activities of the Cybercrime Incident Reporting Points of Contact since ideally, the ordinary Ghanaian for fear of vilification is not cultured to report such incidents. This further supports the argument that perhaps there are more cases than reported as discussion in the social environment indicates how often people fall victim to these scammers.
Here are some steps individuals can take to prevent cybercrime:
- Use strong passwords: Create strong and unique passwords for each online account and use a password manager to help remember them.
- Keep software up to date: Regularly update your operating system, web browser, and other software to keep your computer and devices secured.
- Use antivirus software: Install reputable antivirus software and keep it updated to protect your computer from viruses, malware, and other online threats.
- Be careful what you click: Don’t click on suspicious links or download attachments from unknown sources, and be cautious when clicking on links in emails or on social media.
- Use two-factor authentication: Enable two-factor authentication for all online accounts that support it to add an extra layer of security.
- Protect personal information: Be cautious about sharing personal information online, and never give out personal or financial information to unsolicited callers or emails.
- Backup data: Regularly back up data to an external hard drive or cloud-based storage to protect against data loss from cyberattacks.
- Educate yourself: Stay informed about the latest cyber threats and how to protect yourself against them. Attend seminars, webinars, or training sessions that teach cybersecurity.
- Secure home network: Protect the home network with a strong password and encryption, and regularly check the connected devices to ensure they are secured.
- Report cybercrime: Report any cybercrime or suspicious online activity to the appropriate authorities, such as the FBI’s Internet Crime Complaint Center or local law enforcement.
CONCLUSION
Cybercrime is a very broad concept underneath its multitude of crimes committed with the use of the internet or computer devices; crimes targeted at the computing devices or internet and crimes in which a computer or internet is used as an accessory fall. Crimes like Digital/Cyber extortion, Indecent Image of a Child/Sexual Exploitation, Malware, Fake news to endanger life and property, Charlatanic adverts, Intellectual Property Rights (Software piracy), Cyber Violence, Unauthorized Access (Intrusion), and Cyber fraud are all cybercrime. Others include; Cyber laundering, cyber terrorism, Crypto-jacking, Espionage, Stealing, unauthorized modification, etc.
The majority of the populace falls prey to cyber attackers due to ignorance and lack of information on cybercrime and its machination. Ghanaians’ attitude to the use of the internet and technological devices also makes them more susceptible to cyber-attacks. A lot of the populace assumed cybercrime to mean just cyber fraud, which is very far from the truth, in fact completely false. This conception makes other cybercrimes become normalized and poses more damage to individuals and the country due to the lack of awareness among the general population. In the Ghanaian context, cyber fraud is more common, but cybercrime is an umbrella body for a lot of crimes perpetrated using computers or the internet as a medium, as targets or accessories.
The nature of cybercrime and the myriad of problems it causes has made it dominate the media and public conversation in recent years in Ghana especially cyber fraud as Ghanaians are now beginning to come to terms with the whole cybercrime landscape. The increasing technological advancement around the world is an avenue for potential sophisticated cyber threats, especially when cyber security is not put on the center stage and cyber security culture is not developed among the people. The knowledge of cybercrime and the operating procedure of these cybercriminals warrant the national prioritization of cyber security to help prevent or mitigate the impact of cybercrime by securing cyberspace or fight cybercrime in Ghana with strict measures in the form of laws, awareness creation, security culture, investigations, capacity building, and training as well as the establishment of cyber security authority, etc.
Author’s Profile: He is an investigator and Cybersecurity Practitioner. [PhD (Candidate), P-G Law (UK), MSc, Bsc, Dip.] Ghana, UK. The author’s research interests are in IT, Cybersecurity, Law, Artificial Intelligence, Security, and Criminal Psychology.
Recommended Citation: Abdul-Salam, S. (2023). Cybercrime: The Ghanaian Perspective
Please address all correspondence to: Abdul-Salam Shaibu by Phone: at (+233) 026 5308783 and by email at shaibubaba80@gmail.com
REFERENCES
Barfi, K.A., Nyagorme, P. & Yeboah, N. (2018). The Internet Users and Cybercrime in Ghana: Evidence from Senior High School in Brong Ahafo Region. Retrieved on 19th November 2022 from https://digitalcommons.unl.edu/libphilprac/1715/
Brush, K., Rosencrance, L. & Cobb, M. (2021). Cybercrime. Retrieved on 29th November 2022 from https://www.techtarget.com/searchsecurity/definition/cybercrime
Canadian Centre for Cyber Security (2022). An Introduction to the Cyber Threat Environment. Retrieved on February 1, 2023, from https://cyber.gc.ca/en/guidance/introduction-cyber-threat-environment
Domeher, D., Frimpong, J.M, & Appiah, T. (2014). Adoption of financial innovation in the Ghanaian banking industry. African Review of Economics and Finance Vol. 6, No. 2, pp. 88–114. Retrieved on 8th March 2023 from https://www.google.com/search?q=how+technology+is+been+used+in+ghana+in+banking+and+finance&oq=how+technology+is+been+use+in+Ghana+in+banking+and+finace&aqs=chrome.1.69i57j33i10i160l3.33013j0j9&client=ms-android-transsion&sourceid=chrome-mobile&ie=UTF-8
Gotev, G. (2020). Georgia Reports massive cyber-attack “carried out by Russia”. Retrieved on 13th March 2023 from https://www.euractiv.com/section/eastern-europe/news/georgia-reports-massive-cyber-attack-carried-out-by-russia/
Kemp, S. (2022). Digital 2022: Ghana. Retrieved on 8th March 2023 from https://datareportal.com/reports/digital-2022-ghana
McMillan, R. (2022). Uber says it is a victim of Lapsus$, a hacking group motivated by fame, not money. Retrieved on 13th March 2023 from https://www.livemint.com/technology/tech-news/uber-says-it-is-victim-of-lapsus-a-hacking-group-motivated-by-fame-not-money/amp-11663678455171.html
Omondi, G. (2020). The State of Mobile in Ghana’s Technology Ecosystem. Retrieved on 8th March 2023 from https://www.gsma.com/mobilefordevelopment/blog/the-state-of-mobile-in-ghanas-tech-ecosystem/
Roguski, P. (2020). Russian Cyber Attacks Against Georgia, Public Attributions and Sovereignty in Cyberspace. Retrieved on March 13, 2023, from https://www.justsecurity.org/69019/russian-cyber-attacks-against-georgia-public-attributions-and-sovereignty-in-cyberspace/
Sasu, D.D. (2022). Number of mobile connections in Ghana 2017-2022. Retrieved on 8th March 2023 from https://www.statista.com/statistics/1171461/number-of-mobile-connections-ghana/
Zachary, P. (2014). Black Star: Ghana, information technology development in Africa. Retrieved on 8th March 2023 from https://firstmonday.org/ojs/index.php/fm/article/view/1126/1046


Worthy of reading. It is enrich with information
A very enlightening article. Well written and very informative. Kudos!
Thanks, subscribe through the subscription button and get updates on more of such articles.
Please give us feedback in the comment section. Thank you
Great piece, comrade. I am educated. Regards.
Impressive piece !
Thanks, subscribe through the subscription button and get updates on more of such articles.
This is a great write up. It is hard time people start taking serious measure to protect themselves and their love once from cyber attacks. I must commend you for the suggestion to made on how individuals can protect themselves from cyber attacks. To add to your prevention measures, individual must be carful with the kind of wifi networks they connect their device to especially free wifi service in cafes, hotels, buses, airport among others. Alway make sure to connect to a secure network.
Thanks, your suggestions are welcome. we look forward to giving you the best research articles.