The technological revolution did not arrive with only development-driven initiatives but also brought sophistication to criminal activities. It can be said that technology has revolutionized the traditional way of criminality into a more worldly one called cybercrime, where one can be physically located in Ghana and commit a crime in another country or any part of the world. That is how complex cybercrime is and how it continuously evolves into a more complex enterprise. Though crime has existed since its creation, cybercrime is argued to be the brainchild of technology. Anyway, technology is not to blame for cybercrime, as the idea behind it was development-motivated, but people with criminal mindsets are equally motivated to utilize any means available to perpetrate their criminal activities, hence the emergence of cybercrime.
The continuous evolution of cybercrime and the myriad of destruction it does to an economy (that is, to individuals, organizations, institutions, businesses, and governments) has generated the need to curb the practice by way of protecting cyberspace and any other medium through which the cybercriminals operate.
The ideas for combating cybercrime, such as laws (Substantive law, procedural law, and preventive law), investigation, creating awareness, capacity building and training, establishing cyber security authority, and building cyber security culture, among others, collectively sum up cyber security. The general conversation surrounding cyber security in the world is necessitated by cybercrime and its effects on economies worldwide. For instance, statistics from the Cybercrime Unit of the Criminal Investigation Department of the Ghana Police Service indicate that Ghana lost $273.5 million to cybercrime activities from 2016 to 2022. Also, the massive cyberattack on Georgia in 2019, which is argued to have knocked out up to 15,000 state, private, and media websites as well as the national television station and even court websites containing case materials and personal data affected, raises a huge concern about the urgent need to prioritize cyber security as not just an individual or personal problem but a national security issue. The fact that technological advancement is not ceasing, cybercriminals will continue to exploit the loopholes, which has prompted academia to introduce a full programme of study on cyber security. To fully appreciate the need to give cyber security the maximum attention, the effects of cybercrime on the general economy are espoused below as a precursor to the concept of cyber security, Ghana’s journey, and how cyber security drives economic development.
GHANA’S DIGITALIZATION DRIVE AND EFFECTS OF CYBERCRIME ON THE ECONOMY
The effect of cybercrime on businesses and the economy is highly multifaceted. The very effort of digitalizing an economy also creates more avenues for cybercriminals, posing a huge problem to the economy it seeks to develop. A look at Ghana’s digitalization drive and the problems therein that could affect and thwart the whole economic development agenda.
The introduction of the paperless ports system, means the import processes are now done via an online system, that captures all relevant import information on a database called the ICUMS (Integrated Customs Management System). Traders can obtain required import licenses, permits, and certificates before the arrival of goods, as well as pay fees, among other things. Additionally, a risk clearance system is used to control transaction selectivity and allow automated customs release without scanning or physical inspection. This has created another avenue for cybercriminals to perpetrate their activities by hacking the system and altering import licenses, permits, and certificates to avoid paying the required fees. For instance, in April 2023, during an undercover investigation on stolen vehicles, a hacker told investigative journalist Mariana Van Zeller of the National Geographic Channel that he could hack into the system of the Customs Division to help the syndicate get away with paying the required import duties.
As a result of the widespread adoption of mobile money, and other digital payment systems in Ghana, the Government introduced the Ghana.gov digital services and payments platform to allow Ghanaians to send money to various government ministries and organizations. This is meant to provide a single point of access for all government services provided by departments, ministries, and other organizations.
The Digital property addressing system, dubbed the GhanaPostGPS, is a global addressing system, that divides Ghana into grids of 5m x 5m squares and assigns each one a unique address, known as a digital address. With this system, every piece of land and property will get a permanent address. The system is location-based and is expected to enhance an effective means of providing an address to every location and place in the country, including undeveloped parcels of land, using an information technology application (app). The app generates a unique code for every property or location in Ghana with the use of Global Positioning System (GPS) technology (Bokpe, 2017).
Tiered License Categories, Merchant Account Categorization, and the GhQR. The Tiered License Category is a License Application Pack that provides various license categories for payment service providers. It is anticipated that it will provide various client groups in Ghana with cutting-edge digital banking services. Small and Medium Enterprises (SMEs) have the chance to obtain merchant accounts that are suited to their needs thanks to the Bank of Ghana’s three-tiered Merchant Account Categorization system. A countrywide QR code payment solution called GhQR has made merchant payments easier and cut down on the use of cash. Ghana’s financial institutions and payment service providers now have access to this integrated solution.
Mobile Money Interoperability (MMI) systems enable customers to make a transfer between two mobile money accounts held at different mobile money providers (MMP), for instance, Vodafone Cash and MTN Mobile Money, AirtelTigo Cash and Vodafone Cash, or between an MMP and a bank. The service known as MMI enables quick and easy money transfers between mobile money wallets over different networks. It allows the transfer of funds from a wallet into a bank account and e-zwich cards; and from wallets and e-zwich cards to a bank account. The mobile money system is believed to be growing very fast, and so is mobile money fraud.
The Regulatory sandbox by the Bank of Ghana is available to banks, specialized deposit-taking institutions, and payment service providers, including dedicated electronic money issuers, to provide a forum for financial sector innovators to communicate with the industry regulator to evaluate innovations in digital financial services while assisting in the expansion of the regulatory environment and expertise.
E-justice is where technology, information, and communications are used to improve access to justice and effective judicial actions. Requisitioning, ordering, and buying products and services online is known as electronic procurement, sometimes known as supplier exchange. It is a business-to-business process. E-procurement eliminates the need to manually carry out laborious, procurement-related tasks such as e-Auctions and e-Tenders, exchanging supplier contracts, and filling out supplier onboarding questionnaires. The process works by connecting various entities and processes through a centralized platform. One of the most crucial elements of e-procurement is vendor/supplier management. It involves both supplier relationship management and supplier information management (Awati, & Pratt, 2021).
As announced by the Bank of Ghana, it had partnered with Giesecke+Devrient to pilot a retail central bank digital currency in Ghana. The e-cedi is said to complement and serve as a digital alternative to physical cash. During its piloting, the e-CEDI was tested with banks, payment service providers, merchants, consumers, and other relevant stakeholders.
Through the creative use and application of information and communication technology, the national identification system, which is run by the National Identification Authority, aims to collect personal and biometric data, ensure the protection of enrollees’ privacy and personal information, and provide a complete value-added integrated multi-sectoral and multipurpose National Identity System to support Ghana’s social, economic, and political development.
The government of Ghana wants to digitalize fiscal revenue collection, support a cashless society, and enhance online education delivery, according to the International Trade Administration (ITA, 2022). It also wants to invest in the national fiber network backbone to increase and improve internet connections. Another top objective is to encourage Ghanaian tech entrepreneurs in their efforts to establish tech hubs and export IT-enabled services like business process outsourcing (BPO).
Most recently, the introduction of E-VAT by the Ghana Revenue Authority to digitalize the collection of value Added Tax, which is an electronic means of issuing value Added Tax receipts or an electronic invoicing system for VAT-registered businesses, This, according to the Ghana Revenue Authority, is to enhance record keeping, otherwise known as bookkeeping, reduce the cost of compliance, ease filling, and simplify the VAT refund process.
These digitalization initiatives have invited more cybercriminals into that space and created a herculean task for the Ghana Police Service, considering how porous cyberspace is, especially in Ghana. The fact that digitalization creates avenues for cybercriminals to operate cannot be used as a justification to downplay the many benefits derived from digitalization. It is of note that digitalizing an economy or a country creates cyber-related problems in as much as it resolves another problem. It increases cybercrime cases, especially in any environment with porous cyberspace. The increase in cybercrime activities largely affects businesses and economies in multiple ways. The Ghana Police Service is very aware that the actual cost of cybercrime is really difficult to accurately assess and quantify due to the non-reportage of many cybercrime cases, yet a fair argument on the effect of cybercrime on the economy can be made based on the available figures, for instance.
The increasing incidence of cybercrime discourages foreign investors from establishing businesses in countries tagged as hubs for cybercrime activities. The negative image cybercrime hangs on a country goes a long way toward affecting the economy by preventing foreign investment, as every business thrives in a conducive and hygienic business environment that is extended to cyberspace, as most businesses are operating in that space. For instance, credit and payment systems, e-commerce, etc. In an era where digitalization is on the rise, any criminal activity that targets the internet—in this case, cybercrime, stifles business growth. Aside from discouraging investors, businesses will not be motivated to adopt technologies for innovation considering the huge threat of cybercrime.
According to the INTERPOL (International Police) Unit of the Ghana Police Service, a series of reports of cybercrimes, mostly cyber fraud, are often received from member countries for investigation. Usually, victims in those countries had lost money to cybercriminals whose identities or locations had been traced to Ghana. Some of these cases include; romance scams, gold scams, investment fraud, inheritance schemes, etc.
There are instances like email compromise, where victims (usually companies) in Ghana think they are dealing with their counterparts in other countries but will end up losing huge sums of money to these cyber criminals, who divert the funds to different bank accounts belonging to their criminal syndicate. Most of these perpetrators are usually traced to Ghana.
The financial losses due to cybercrime are very significant, and businesses also suffer other disastrous consequences as a result of the activities of cybercriminals. The consequences come in the form of damaging brand identity and reputation, damaging investor confidence, and a potential drop in the prices of shares. Businesses may also be sued for data breaches that may result in fines and penalties. Its effects on a country’s public health and national security cannot be overemphasized (Brush, Rosencrance, & Cobb, 2021). Similarly, Tunggal (2022) strongly believes cybercrime badly affects businesses, institutions, and governments through economic loss and reputational damage. Theft of intellectual property, business information, and trading interruptions cost a lot of money to fix, which results in a decline in consumer confidence, a loss of existing and potential consumers to rivals, and negative media attention. For instance, in May 2017, a cyberattack involving the “WannaCry” Ransomware affected many notable organizations globally. Experts argued that this attack is the world’s biggest single cyberattack incident, considering the damages caused and the number of countries affected. Nearly 200,000 computers and databases belonged to various organizations, and at least 150 different nations were impacted (Media Foundation for West Africa, 2017).
Figure 1: Global Cybercrime Trends and Reports
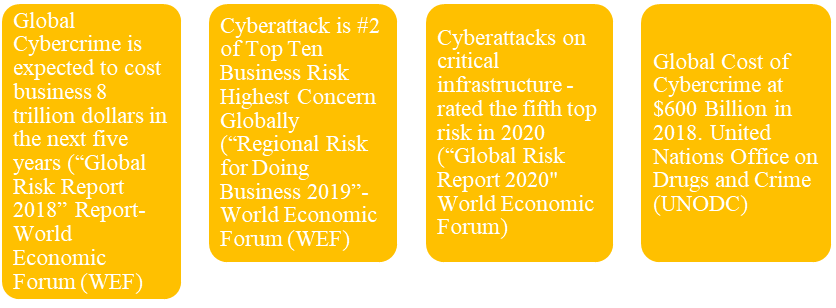
In the Ghanaian context, the issue of cybercrime continues to cause unending havoc and thwart the development of the country. A testimony to this is the recent incident when the Electricity Company of Ghana’s (ECG) prepaid software was reportedly hacked. This prevented customers from vending and purchasing prepaid for close to a week, and the attack on the electronic transmission system of the Ghana Electoral Commission during the 2016 election was reported by the Chairperson. The economic losses and damages that occurred during that period were difficult to quantify. According to the Media Foundation for West Africa (2017), Ghana has been blacklisted by many significant international e-commerce companies and online retailers, including Amazon, PayPal, and other online retail stores. Residents in Ghana are unable to purchase goods and services from some international online shops with their credit cards because of cyber fraud.
According to the former Director of the Cybercrime Unit at the CID, Dr. Gustav Yankson, cybercrime activities in Ghana, especially fraud alone, constituted 60 percent of crimes recorded daily, and the country lost 35 million dollars to fraud in 2016. In 2017, an amount of 69 million dollars was lost, while 97 million dollars were lost by August 2018 (Ghana News Agency, 2018). Giroud (2021) argued that the incidence of cybercrime is obstructing the development agenda of the country, as data from the E-Crime Bureau indicates an estimated cost of US$230 million to the country over the period from 2016 to August 2018. These statistics indicate the increasing incidence of cybercrime in Ghana, which corroborates the assertion that the lack of awareness of risks in the internet space, has contributed to the increase in cyberfraud cases in the country. It has emerged that a total of $19.8 million was lost by victims as a result of the activities of cyber fraudsters in the country in 2020, $20.3 million in 2021, and $19.7 million in 2022. Comparatively, in 2019, the total amount lost to cyber criminals was $11 million (Cybercrime Unit, of Ghana Police Service, 2022).
Figure 2: Monies lost to cybercrime in Ghana from 2016–2022.
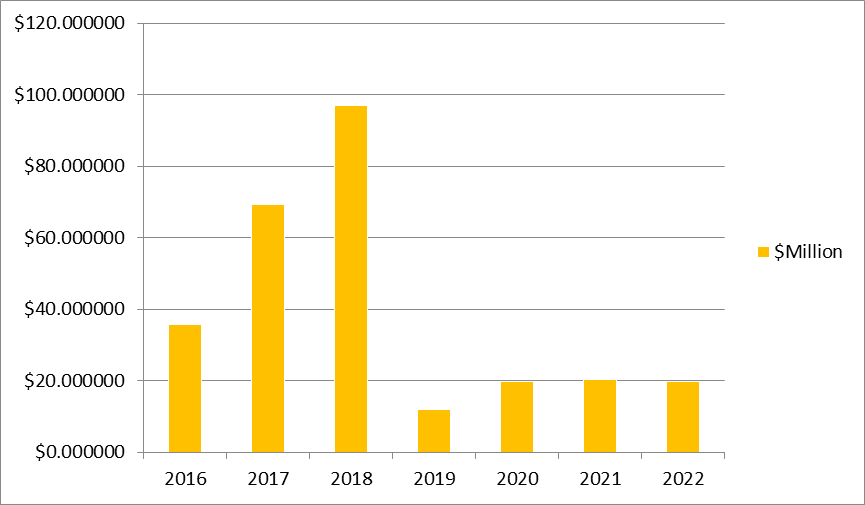
Source: The Cybercrime Unit of the Criminal Investigation Department, Ghana Police Service.
Figure 2 above gives a breakdown of monies lost to cybercrime from 2016-2022. The decrease in monies lost, as indicated in Figure 3, is a reflection of the efforts of the Ghana Police Service and other institutions created to intervene in protecting cyberspace, but that is not to say cyberspace has been fully secured. The constant increase and decrease in the monies lost to cybercrime in Ghana from 2016 to 2022 justify the need to intensify the fight against cybercrime and consolidate the gains made during the period that resulted in a decrease in monies lost. The various institutions, including the Ghana Police Service, should be recommended for tremendous work, looking at the amount lost to cybercrime in just three years (2016–2018), which is over 201 million dollars, as against four years (2019–2022), amounting to about 70.8 million dollars. This indicates how well the institutions created to curb the menace are working to make cybercrime unattractive.
COMBATING CYBERCRIME: THE CONCEPT OF CYBERSECURITY
The issue of cyber security has become incumbent on every nation and, by extension, businesses and individuals since cybercrime has become an existential threat to the world. Wilczek (2020) justified the urgent need for cyber security to be prioritized with the argument that cybercrime is surpassing world-established multinational firms and companies in revenue generation.
De Groot (2022) posits that cyber security is a body of technologies, processes, and practices designed to protect networks, devices, programs, and data from attack, damage, or unauthorized access. De Groot further states that cyber security can be referred to as information technology security. According to Kelley (2022), the field of cyber security deals with ways to protect systems and services from malicious online actors, including hackers, spammers, and cybercriminals.
Given the above, cyber security can be argued to mean the continuous process, mechanism, strategies, and techniques constantly designed to protect, detect, and retrieve computer systems, information, networks, devices, and programs from attacks, damage, and unauthorized access. This means cyber security is not only about protecting computer systems, information, networks, devices, etc. from cyber threats and cybercriminals, but also about building mechanisms for backups in the unlikely event that the unfortunate happens, as well as sensitizing people, businesses, and institutions to be able to identify threats and act accordingly in order not to fall victims. Cybersecurity is a continuous process because cyberattacks are increasingly sophisticated and evolving, hence the need to constantly upgrade the strategies, systems, and techniques aimed at protecting cyberspace to meet prevailing conditions.
Cybersecurity plays a critical role in developing the global economy at a time when the digital economy is undergoing a paradigm shift. This development has awakened stakeholders in cyberspace to secure space from threats and attacks to maximize the full potential of information and communication technology to develop their economies. Preventing cybercrime is not only an individual responsibility but also a national security issue. Here are some steps a country can take to prevent cybercrime:
- Create a national cybersecurity strategy outlining goals and objectives.
- Create a national cybersecurity agency for strategy implementation.
- Increase cybersecurity awareness through campaigns to protect citizens.
- Enhance cybersecurity education to train future experts.
- Develop robust cybersecurity policies and standards for government agencies, critical infrastructure providers, and other organizations.
- Promote international cooperation to share information and collaborate on cybersecurity initiatives.
- Increase investment in cybersecurity research and development to stay ahead of evolving cyber threats.
- Develop incident response plans to respond effectively to cyber incidents and reduce the damage caused by them.
- Enact laws and regulations to ensure compliance with cybersecurity standards and punish cybercriminals.
- Conduct regular cybersecurity audits to identify vulnerabilities and enhance the cybersecurity posture of critical infrastructure and government agencies.
Also, preventing cybercrime is a responsibility that falls on individuals as well as organizations and governments. The fight against cybercrime cannot be left to only the government and institutions, there is a need for individuals to get actively involved to complement the efforts of the government. This is because the negligence and security unconsciousness of individuals can render government intervention in protecting cyberspace fruitless, hence the need for a collaborative effort between the government and the general populace, who are the end users.
Ramachandran (2019) outlined the following as ways in which cyberspace can be secured worldwide:
- Enterprises must implement secure practices to produce products and services and educate employees on safety.
- Governments should educate citizens on cyber security, align risk management and IT activities, and regulate private and public enterprises for compliance.
- Countries must voluntarily adhere to acceptable cyber norms and international law for responsible state behavior to enhance predictability and stability in cyberspace, as outlined in the US National Cyber Strategy of 2018.
- Countries should cooperate to have a secure cyberspace and allow legitimate requests for the extradition of criminals located abroad.
- Companies, academia, and industry associations like ISACA must develop and maintain skilled cyber security personnel.
- Countries should build strong detective and deterrence capabilities in cyberspace, in addition to having a robust incident response mechanism.
- Enterprises should follow the National Institute of Standards and Technology Cybersecurity Framework and ISACA guidelines for benchmarking best practices.
- Countries should promote internet freedom, a multi-stakeholder governance model, and interoperable communication infrastructure for a robust information and knowledge economy, ultimately leading to a prosperous global economy.
Baylon and Antwi-Boasiako (2016) admonished that electronic waste is destroyed or data on devices is wiped out before they are exported. They argued that to tackle cybercrime stemming from electronic waste, there must be greater efforts to destroy, wipe, or clean the memories of devices before they are exported, or better yet, physically destroy the hard drives with a hammer or other blunt instruments. Additional software that erases the hard disks can be employed. According to Baylon and Antwi-Boasiako (2016), to successfully secure cyberspace from cybercriminals with regards to cybercrime that stems from electronic waste, it is incumbent on governments of countries that export electronic waste to launch a public education campaign since most people are ignorant that the data remaining on their used devices could end up in the hands of cybercriminals. They strongly maintained that firms that recycle electronic waste for export and those that manufacture devices should be encouraged, if possible, to recycle used devices instead of exporting them, as this is the most assured way of preventing cybercriminals from obtaining data on these devices to exploit them.
To put cyber security in a proper perspective, to secure cyberspace or to fight cybercrime in Ghana, strict measures in the form of laws, awareness creation, security culture, investigations, capacity building and training on cybercrime, as well as the establishment of cyber security authority, should be of utmost importance to serve the purpose of protecting the cyberspace;
Laws: To defeat cybercrime in any environment and protect cyberspace, strict laws should be passed to deal with activities that pose a threat to cyberspace. Regulations to lower the risk and/or mitigate the harm done to people, organizations, and infrastructure due to cybercrime should be included in the law. These regulations should also cover the use of the internet, computers, and related digital technologies, as well as the actions of the general public, the government, and private organizations. Accordingly, the law must include substantive, procedural, and preventive laws (United Nations Office on Drugs and Crime, 2019). Substantive law here means the law must spell out specific acts that are deemed illegal and, as a result, warrant punishment. This is because a person cannot be punished for an act that was not prescribed by law at the time the person committed the act; procedural law is the process and procedures to be followed in the application of the law and the rules to enable the enforcement of the law. Preventive law focuses on preventing cybercrime or mitigating the damages resulting from the commission of the crime. The law ought to be tough and punitive enough for payment providers found negligent about cybercrime. Therefore, laws with strict enforcement are a prerequisite for cyber security; the nature and type of laws are country-specific and dependent on the problem at hand.
Investigations: Once laws are made in the bid to protect cyberspace, institutions responsible for the implementation and enforcement of the laws must be fully equipped with logistics and training and be motivated to be able to investigate and apprehend perpetrators of cybercrime. There should be specialized cybercrime investigators to act proactively in investigating and analyzing potential threats in order to prevent or mitigate the damages that are caused by cybercriminals. Investigations should not only be conducted in a reactive manner when harm has already been done. The best way to use investigation to secure cyberspace is for it to be largely proactive to prevent damages while putting in a strenuous effort to also investigate, apprehend, and prosecute perpetrators to deter potential offenders from engaging in the cybercrime trade.
Awareness creation: To effectively fight cybercrime, there must be a serious awareness creation among the citizens to make them well informed on cybercrime and get them equipped on cyber security. There is a need to educate the general populace because they are the users of these technological and digital devices and are prone to cyber-attacks when ignorant because the people are those who make institutions secure, not technology. No one is immune to a cyber incident or one “bad click.” We must increase awareness at all ages and levels, regardless of industry. It is crucial to start educating kids about cybersecurity in particular. In this era of rapid technological advancement, children need to immerse themselves in technology at a young age to learn the skills they will need throughout their lives. To fully take advantage of this chance, they must be given the necessary tools, protection, and knowledge of the hazards. Governments and the private sector should collaborate to work toward unified awareness campaigns. Furthermore, users should never be the last line of defense in cybersecurity, as they need to play a role in educating each other and amplifying the reach of awareness campaigns (World Economic Forum, 2020).
As part of cyber security awareness, it is suggested that institutions, businesses, and organizations maintain the most recent version of their software, use anti-virus software and a firewall, make use of strong passwords and a password management tool, use two-factor or multi-factor authentication, and make staff understand phishing scams. Pamphlets, phone calls, and emails all need to be handled with caution. Whether you are concerned about ransomware, remote working, insider threats, or any other risk, you must review your security measures and determine whether they are fit for the current environment. That could mean testing your infrastructure to identify possible vulnerabilities, updating documentation to bolster general data protection regulation compliance, and improving employees’ security and data awareness through training.
Cyber capacity building and training: Creating cyber security awareness among the people can be maximized when the people and institutions operating in cyberspace, as well as the regulatory institutions’ abilities to detect, investigate, and respond to threats, are built. Cyber capacity building and training can be actualized to secure cyberspace through programs, including training on cyber attribution and the framework of responsible state behavior, strengthening international partnerships, and encouraging excellent practices that uphold rights while defending the security of cyberspace. Also, cyber capacity building and training can be achieved by establishing and strengthening cybersecurity incident response teams, developing and implementing national cyber strategies and policies, and raising awareness of cyber security (Naylor, Painter, & Hakmeh, 2022).
Critical infrastructure needs to be strengthened. With these elements in place, people can utilize the Internet, with the danger of malware and similar threats reduced. Awareness creation through education and information sharing is vital for good cyber hygiene and sustainable cyber capacity. This must be done on all levels, from the grassroots to the top echelons, in all departments and sectors, from legislation to the creation of new departments and infrastructure. The ability to communicate this information is a central factor. Educators, means, and funds are needed to achieve this goal. Being able to locate the right partners to create awareness of the importance, willingness, and political stability of cyberspace is a key factor in building cybercapabilities. Education, learning, sharing, and cooperation are central to success (Muller, 2015).
Establishing cybersecurity authority: To secure cyberspace, it is a necessity to establish a body that will be responsible to regulate cybersecurity activities; preventing, managing, and responding to cybersecurity threats and regulating owners of critical information infrastructure about cybersecurity operations, service providers, and practitioners; fostering the growth of cybersecurity in the nation to maintain a secure and resilient digital ecosystem; establish a platform for cross-sector engagements, on matters of cybersecurity for effective coordination and cooperation between key public institutions and the private sector; create awareness of cybersecurity matters; and collaborate with international agencies to promote cybersecurity of the country. Without establishing a cybersecurity authority that will spearhead the campaign, securing cyberspace will face tremendous setbacks and failure.
Cybersecurity Culture: All measures aimed at securing cyberspace can be implemented, but without the right or good cybersecurity culture, all the efforts will not yield any positive results because people make an organization secure, not technology. A strong cybersecurity culture starts with building awareness and encouraging best practices in cyber hygiene, normalizing these behaviors so they become second nature to people. Building a culture of awareness, trust, and knowledge in an organization means incidents are less likely to occur, and if they do, the people will be much more prepared to deal with the fallout quickly and effectively to minimize any financial, technical, or reputational damage. The cybersecurity culture of an organization encompasses the knowledge, awareness, attitudes, and behaviors of employees regarding the threat landscape, cybersecurity, and information technologies (Duggal, 2022). A strong cyber security culture is one in which the organization’s approach to cyber security is supported by both the organizational determinants of culture (policy, process, leadership, social norms, etc.) and the individual determinants of culture (attitudes, knowledge, assumptions, etc.) and is reflected in cyber security conscious behaviors (Everard, 2021).
GHANA’S CYBERSECURITY IN PERSPECTIVE
The Ghanaian perspective on cyber security has been the institutionalization of policies and strategies aimed at educating and creating awareness of the cyber threat, arresting cybercriminals, and recovering the proceeds of cybercrime. Also preventing data theft, attacks on computer systems, software, and network devices, and retrieving data. Again, the police service makes the business of cybercrime distasteful, unpleasant, and unattractive to the general population to make the digitalization drive seem smooth. This is evident in the various approaches that have been employed to tackle cybercrime in the country. The story of cyber security in Ghana has been policy upon policy, act upon act, and strategies upon strategies, a reflection of how relentlessly various institutions, especially the Police Service, are working to meet prevailing conditions in the fight against cybercrime. The Cyber security policy of Ghana seeks to address the major cyber risks facing Ghana from attacks on the national information infrastructure and again address the lack of awareness of the risks users and businesses face doing business in cyberspace. The policy also addresses the need to develop a technology framework for combating cyberattacks and capacity building for cyber security experts to make Ghana self-sufficient in the fight against cybercrime and, in the near future, create a culture of cyber security in Ghana. A journey to the specific interventions adopted and implemented in the quest to secure cyberspace in Ghana includes:
The Ghana Police Service, as a crime detection and prevention institution, has a Cyber Crime Unit that is primarily responsible for detecting and investigating crimes whereby digital devices, networks, and other telecommunication devices or the internet space are the target or the means to perpetrate the crime. Over the years, the Cyber Crime Unit has been investigating and prosecuting cybercriminals, collecting data and undertaking forensic analysis, conducting cyber intelligence collection, analysis, and dissemination, assessing and analyzing cybercrime phenomena, and surveilling and monitoring the cyberspace, which to a greater extent appeared to be yielding results in the area of the amount of money lost on cybercrime since 2018, as seen in figure 2. The Police Service, as part of their intervention to secure cyberspace, has arrested and prosecuted some people who are perpetrators of this crime. Notable among them are Rosemond Brown (Akwapem Poloo) for child pornography, Patricia Oduro Koranteng (Nana Agradaa) for a charlatanic advertisement, Patrick Asiedu (the alleged doctor) for spreading fake news, Solomonn Doga (a phone repairer) for sextortion, and a host of other cases of arrest and prosecution.
Fighting cybercrime with the law in Ghana dates back to 2008, when the Electronic Transaction Act (ETA 2008) was passed by parliament. The Act specifies legislation on cybercrime and prescribes punishment for cybercrime perpetrators. The Act outlined cyber offenses, which include but are not limited to: stealing, charlatanic advertisement, attempt to commit crimes, aiding and abetting, a duty to prevent a felony, conspiracy, forgery, intent and criminal negligence, access to a protected computer, obtaining electronic payment mediums falsely, electronic trafficking, and possession of electronic counterfeit-making equipment, etc. The Act addresses issues in the fight against cybercrime as well.
The Data Protection Commission was established as an independent statutory body under the Data Protection Act, 2012 (Act, 843) to protect the privacy of individuals and personal data by regulating the processing of personal information. The commission was mandated to provide for the process to obtain, hold, use, or disclose personal information and for other related issues bordering on the protection of personal data. To undertake regular vulnerability and system audits to ensure the robustness of IT systems that store, process, or transmit personal data. The Data Protection Act ensures the protection of private data of the government, citizens, and businesses in Ghana. The Data Protection Commission has recently been particularly proactive in its enforcement proceedings, which has prompted numerous data controllers to register and adhere to the Data Protection Act’s obligations (The Media Foundation for West Africa, 2017).
Again, the National Computer Emergency Response Team (CERT) was established and inaugurated in 2014 by the Ministry of Communications to coordinate cyber incidents and assist in resolving future incidents within the government network. The establishment of CERT-GH is a critical component of the cyber security emergency readiness of the National Cyber Security Policy and Strategy (Media Foundation for West Africa, 2017). On the business side, the presence of the e-Crime Bureau in Ghana has greatly helped the course of cyber security in the country. Organizations can investigate cybercrime thoroughly, which has largely improved the protection of cyberspace.
The Subscriber Identity Module (SIM) registration by the National Communication Authority is another initiative to mitigate cybercrimes committed using mobile phones. There is currently another directive by the Ministry of Communication for the telecommunication companies in Ghana to reregister SIM cards with only Ghanaian cards as the accepted identity card for registration. This exercise is purposely designed to fight cybercrimes that are perpetrated using SIM cards by making it easier for the Ghana Police Service, through the Cybercrime Unit, to trace and arrest such criminals and aid in alleviating cybercrimes and other related crimes. Government programs aimed at reducing crime in general and computer crime, in particular, include the Economic and Organized Crime Office (EOCO) under the Attorney General’s Department and the Financial Intelligence Center for the banking industry.
The losses incurred by banks in Ghana due to cybercrime activities and the threat it poses to the banking sector motivated the Bank of Ghana to issue a Cyber and Information Security Directive in 2018 to protect the banking sector and financial institutions under its supervision from cybercrime and its related challenges. The directive obligated the various institutions it regulates to
- Place special emphasis on cyber and information security and take all the necessary steps to protect and manage their systems and data effectively.
2. Expand and enhance their cyber and information security capabilities.
3. Enhance the institution’s resilience to cyber and information security risks, reducing business continuity impact, and minimizing damage to ICT assets and customers.
4. Determine the extent of the implementation process by financial institutions while seeking to maintain, at the same time, a degree of flexibility as required by the unique nature of this Directive(s).
5. Institutions must manage cyber and information security risks systemically, following Ghanaian law and Directives on risk, operational risk, business continuity, and ICT management.
6. In managing its operational risks, the institution shall address and document the cyber and information risks relevant to its operations as well as the measures taken to mitigate them.
7. Address cyber and information security scenarios that may affect its activities and those of customers, suppliers, and service providers.
8. Understand the scope of cyber and information security threats and the required security capabilities for meeting this challenge.
9. All institutions supervised by the Bank of Ghana shall be International Organization for Standardization (ISO) 27001 certified and should adopt ISO 27032.
10. Institutions that handle, process, store, or transmit debit cards, credit cards, prepaid cards, e-purses, ATM cards, and/or POS) and related information shall be certified.
11. The methodology for managing and handling cyber and information security events shall comply with international standards such as those of the National Institute of Standards and Technology (NIST) and ISO 27001.
Ghana’s cyber security activities have not gone unnoticed, as according to the Acting Director-General of the Cyber Security Authority, Dr. Albert Antwi-Boasiako, commendations have come in from the World Bank, World Economic Forum, UNICEF, and the ECOWAS Commission, among others, with the ECOWAS Commission requesting Ghana to lead cyber security efforts in the African sub-region. He issued a caveat that there is still work to be done to firmly secure cyberspace, irrespective of the recognition so far (Gyesi, 2020). On the 2020 Global Cybersecurity Index (GCI) of the International Telecommunication Union (ITU), Ghana received an overall score of 86.69%, placing third in Africa (Boakye, 2021).
HOW CYBERSECURITY DRIVES ECONOMIC DEVELOPMENT
Fraser, (2020) posits that the global economy is dependent on technology and driven by digital infrastructure. Technological innovations coupled with cyber security help businesses pursue their value chain activities and turn a profit for their owners and shareholders. Securing cyberspace makes it more conducive and hygienic for businesses to thrive. At the rate at which businesses are moving online and exploiting technological systems, securing cyberspace appears to be indispensable. The profits and expansion witnessed within the business space among both private and state-owned businesses in the digital economy are attributed to the protection of cyberspace. This, by extension, means that without cyber security, the growth of the digital economy would be halted, truncated, or unhygienic. This is evident in the report by Ramachandran, (2019), that global e-commerce is growing at a phenomenal rate, as 1 billion consumers were expected to make purchases across borders in 2020 (compared to 390 million in 2016), per the Global E-commerce Association.
Oxford Economics (2016) argued that cyber security is more than just an “insurance policy” against hackers, malware, or other threats. They opined that agile, proactive cybersecurity capabilities could help drive growth and innovation. It is thought that a solid cybersecurity foundation is necessary for effective digital transformation. On this basis, businesses will feel secure using digital procedures and technologies that stimulate innovation and expansion. For instance, the paperless port system, which has been implemented in Ghana, contributed to a 3.9% increase in import revenue (from 12.7 billion to ¢ 13.2 billion) from 2017 when it was first implemented to 2018 in just a year of implementation. Without it, companies may hesitate to start digital projects, stifling their innovation potential and opening the door to digital disruptors. This shows cyber security drives economic development, especially in the digital economy; by making cyberspace hygienic, businesses will be motivated to implement processes and technologies that bring growth and development.
Cybercrime is estimated to have caused damages totaling US$6 trillion globally in 2021, as the statistics from Cyber Security Ventures indicate. The amount is argued to be twice the Gross Domestic Product (GDP) of all African countries combined (Media Foundation for West Africa, 2022). In the case of Ghana, from 2016 to 2022, $271.8 million was lost to cybercriminals, according to statistics from the Cybercrime Unit of the Criminal Investigative Department of the Ghana Police. Businesses, organizations, institutions, individuals, and governments incur these losses. Cybercrime is also projected by Cybercrime Magazine to cost the world $10.5 trillion annually by 2025. These monies could have been invested in the global and local economies of the respective countries for economic expansion. In essence, not protecting cyberspace costs the world a huge sum of money through the activities of cybercriminals. What this suggests is that, aside from encouraging businesses to adopt technologies to develop and grow their businesses, monies that could have been lost to cyber criminals would be invested in an economy like Ghana, to propel economic growth. $19.8 million is a huge sum of money that, when invested in a sector, would have a positive impact on the Ghanaian economy.
Cybersecurity drives economic development in the sense that securing cyberspace is an incentive for foreign investors. When cyberspace is secured from attacks, foreigners are motivated to invest in businesses in such a country. When established, these businesses will pay taxes, employ graduates, and increase the country’s GDP. In most cases, these businesses undertake social responsibilities in their host country, which contributes to the development of the country. This argument is supported by a report by CyberSource Corp., a payment processor in the United States, that in 2008, over half of US merchants who accepted international orders refused to process purchases from Ghana, citing fraud concerns (Motiwala, 2017). This would not encourage investors in the credit and payment systems to invest in Ghana, which hinders the growth of local credit and payment systems. Conversely, secured cyberspace would invite investors in the credit and payment systems to Ghana.
Having identified the impact of digitalization on the economy of a country, it is safe to say cyber security contributes to economic development by creating a conducive and hygienic environment for digitalization to thrive. As mentioned earlier, in the case of Ghana, as a result of cyber security, the government has implemented a lot of digitization policies that have contributed to economic growth and the ease of doing business in the country. The paperless port system alone witnessed an import revenue increase of 3.9% (from 12.7 billion to ¢ 13.2 billion) from 2017 to 2018 (Wass, 2019). In the Mobile Money market, MTN mobile money also witnessed 9% year-on-year growth in the first half of 2022 (The Business & Financial Times, 2022). These were achieved partly as a result of the interventions made in the area of cyber security in the country. The information and communication subsector has also witnessed huge growth. This is due to the various cyber security measures being implemented that have offered the players in the sector the opportunity to introduce technological innovations, leading to growth in the sector and a huge contribution to the Gross Domestic Product of Ghana, especially in the year 2020. Below are some excerpts from the telecommunications sector’s contribution to the Ghanaian economy.
Figure 3: Telecom sector contribution to Ghana’s GDP 2020
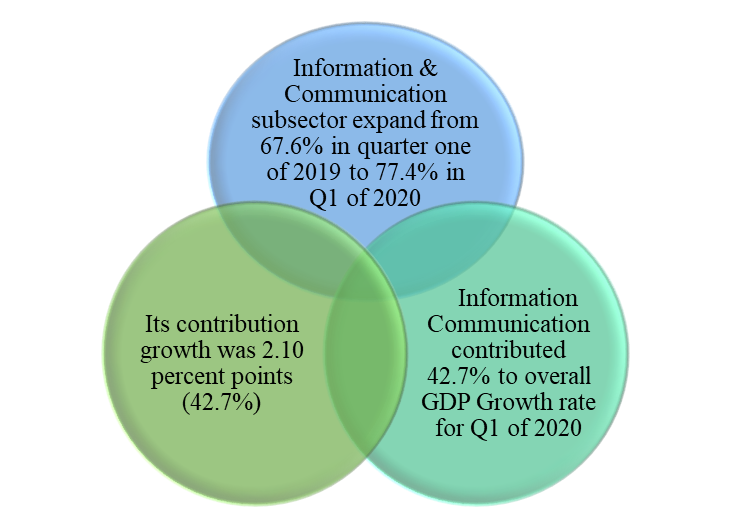
Source: Ghana Statistical Service, 2020.
CONCLUSION
The problem of cybercrime keeps manifesting in different folds as technology keeps advancing, digital devices are embedded in the way of life of the people, and internet penetration keeps soaring without cyberspace protection. This development has raised concerns and necessitated a cybersecurity conversation. Cybersecurity is paramount to economic development considering the huge damages that cybercrime imposes on individuals, businesses, institutions, and governments, which transcend from monetary loss to reputational loss and loss of investors. These losses are potential drivers of economic growth as money lost to cybercrime could be invested to expand businesses and even build capital infrastructure to propel development, whereas reputational loss stifles business growth as it serves as a disincentive to investors, business operations, and customers.
The push for the digitalization of economies has been globally recognized, and as state institutions and governments are assiduously implementing it, avenues are widening for cybercrime activities, which has further created problems emanating from these initiatives. Actualizing its potential benefits to drive economic growth for national development is dependent on securing cyberspace and continuously championing its consolidation. The digitalization policies of Ghana would be meaningless without cyber security in the sense that when cyberspace is insecure, cybercrime will dominate cyberspace, making digitizing the economy more vulnerable. The numerous efforts in digitalizing the Ghanaian economy would not have achieved the gains and recognition they did had it not been for the efforts of various institutions, including the Police Service, to make cyber security a priority. A successful cyber security campaign drives economic growth and national development, as businesses will adopt new technologies for innovation when cyberspace is secured, investors will equally be enticed to invest in businesses, digitalization will be smoothly implemented, and its concomitant benefits will be highly maximized. Secured cyberspace does not only promote economic development but would also place the country in the league of countries doing well in cyber security.
Author’s Profile: He is an investigator and Cybersecurity Practitioner. [PhD (Candidate), P-G Law (UK), MSc, BSc, Dip.] Ghana, UK. The author’s research interests are in IT, Cybersecurity, Law, Artificial Intelligence, Security, and Criminal Psychology.
Recommended Citation: Abdul-Salam, S. (2023). Cybersecurity: A Tool to Drive Economic Development.
Please address all correspondence to: Abdul-Salam Shaibu by Phone: at (+233) 026 530 8783 and by email on shaibubaba80@gmail.com
REFERENCES
Awati, R. & Pratt, M.K. (2021). E-Procurement (Supplier Exchange).Retrieved on 5th December 2022 from https://www.techtarget.com/searchcio/definition/e-procurement
Baylon, C. & Antwi- Boasiako, A. (2016). Increasing Internet Connectivity While Combatting Cybercrime: Ghana as a Case Study. Global Commission On Internet Governance Paper Series: No. 44. Retrieved on 4th December 2022 from https://www.cigionline.org/publications/increasing-internet-connectivity-while-combatting-cybercrime-ghana-case-study/
Brush, K., Rosencrance, L. & Cobb, M. (2021). Cybercrime. Retrieved on 29th November 2022 from https://www.techtarget.com/searchsecurity/definition/cybercrime
Bokpe, S. J. (2017). How the National Digital Property Address System works. Retrieved on 5th December 2022 from https://www.graphic.com.gh/news/general-news/how-the-national-digital-property-address-system-works.html
Boakye, E.A. (2021). Ghana Ranked Third in Africa on Global Cybersecurity Index. Retrieved on 5th December 2022 from https://citinewsroom.com/2021/07/ghana-ranked-third-in-africa-on-global-cybersecurity-index/
De Groot, J. (2022). What is Cyber Security? Definition, Best Practices & Examples. Retrieved on 18th November 2022 from https://digitalguardian.com/blog/what-cyber-security
Duggal, Y. (2022). How to Create a Strong Cybersecurity Culture in your Organization. Retrieved on 9th March 2023 from https://netacea.com/blog/how-to-create-a-strong-cybersecurity-culture/
Everard, T. (2021). What is Cyber Security Culture and why does it matter for your organisation? Retrieved on 9th March 2023 from https://www.paconsulting.com/insights/what-is-cyber-security-culture-and-why-does-it-matter-for-your-organisation
Fraser, D. (2020). Cyber Security is a Driver For Economic Growth. Retrieved on 19th November 2022 from https://www.caribbeannewsglobal.com/cybersecurity-is-a-driver-for-economic-growth/
Ghana News Agency (2018). Awareness Creation on Cyber Crime Key For Digital Migration. Retrieved on 30th November 2022 from https://www.businessghana.com/site/news/general/175484/Awareness-creation-on-Cyber-Crime-key-for-digital-migration
Gyesi, Z.K. (2020). Ghana Records Over 11,000 Cybercrime Cases Since 2019. Retrieved on 19th November 2022 from https://www.graphic.com.gh/news/general-news/ghana-records-over-11-000-cybercrime-cases-in-a-year.html
Giroud, K. (2021). Cyber Security in Ghana: Vigilance First. Retrieved on 19th November 2022 from https://www.globalcyberalliance.org/cybersecurity-ghana/
Ghana Statistical Service (2020). Quarterly Gross Domestic Product (QGDP) First Quarter 2020. Retrieved on 9th February 2023 from https://statsghana.gov.gh/gssmain/storage/img/marqueeupdater/Newsletter%20quarterly%20GDP%202020%20_Q1_June%202020%20Edition.pdf
International Trade Administration (2022).The Ghanaian Government Outlines its Priorities in the Digital/ICT Sector For 2022-2023. Retrieved on 19th November 2022 from https://www.trade.gov/market-intelligence/ghana-digitaleconomy#:~:text=Government%20efforts%20in%20this%20area,improve%20productivity%20and%20service%20delivery.
Kelley, K. (2022). What is Cyber Security and Why It is Important? Retrieved on 18th November 2022 from https://www.simplilearn.com/tutorials/cyber-security-tutorial/what-is-cyber-security#what_is_cyber_security
Media Foundation for West Africa (2022). Ghana’s Cyber Security Law Implementation: CSOs Demand More Awareness Creation. Retrieved on 18th November 2022 from https://www.mfwa.org/issues-in-focus/ghanas-cybersecurity-law-implementation-csos-demand-more-awareness-creation/
Media Foundation for West Africa (2017). Cyber Security in Ghana: Key Issues and Challenges. Retrieved on 18th November 2022 from https://www.mfwa.org/wp-content/uploads/2017/09/cyber-security-Report.pdf
Motiwala, A. (2017). Cyber Security in Ghana: Evaluating Readiness for the Future. Policy Brief 1, Accra: KAIPTC. Retrieved on 18th November 2022 from
https://www.africaportal.org/documents/20657/Cyber_security_in_Ghana.pdf
Muller, L.P. (2015). Cyber Security Capacity Building in Developing Countries. Retrieved on 10th March 2023 from https://www.jstor.org/stable/resrep07959
Naylor, E., Painter, C., & Hakmeh, J. (2022). How does capacity-building make cyberspace better? Retrieved on 9th March 2023 from https://www.chathamhouse.org/2022/02/how-does-capacity-building-make-cyberspace-better#:~:text=Cyber%20capacity%2Dbuilding%20can%20strengthen,Principles%20at%20the%20United%20Nations.
Oxford Economics (2016). Cyber Security as a Growth Advantage. Retrieved on 19th November 2022 from https://www.oxfordeconomics.com/resource/cybersecurity-as-a-growth-advantage/
Ramachandran, R. (2019). Cyber Security and its Critical Role in Global Economy. Retrieved on 19th November 2022 from https://www.isaca.org/resources/news-and-trends/isaca-now-blog/2019/cybersecurity-and-its-critical-role-in-global-economy
The Bank of Ghana (2018). Cyber & Information Security Directive. Retrieved from https://www.bog.gov.gh/wp-content/uploads/2019/09/CYBER-AND-INFORMATION-SECURITY-DIRECTIVE.pdf on February 9, 2023.
The Republic of Ghana (2015). National Cyber Security Policy & Strategy. Retrieved Fromhttps://www.itu.int/en/ITUD/Cybersecurity/Documents/Country_Profiles/National-Cyber-Security-Policy-Strategy-Revised_23_07_15.pdf on 4rd December 2022
The Republic of Ghana (2020). Cyber Security Act, 2020 (Act 1038). Retrieved from https://csdsafrica.org/wp-content/uploads/2021/08/Cybersecurity-Act-2020-Act-1038.pdf on 5th December 2022.
The Republic of Ghana (2008). Electronic Transactions Act, 2008 (Act 772). Retrieved on 5th December 2022 from https://www.researchictafrica.net/countries/ghana/Electronic_Transactions_Act_no_772:2008.pdf
The Business & Financial Times (2022). MTN MoMo Revenue Up 9%. Retrieved on 6th December 2022 from https://thebftonline.com/2022/08/05/mtn-momo-revenue-up-9/#:~:text=Revenue%20of%20the%20mobile%20money,unaudited%20interim%20report%20has%20shown.
Tunggal, A. T. (2022). Why is Cyber Security Important? Retrieved on 18th November 2022 from https://www.upguard.com/blog/cybersecurity-important
The Ghana ICT for Accelerated Development (ICT4AD) Policy (2003). A Policy Statement for the Realization of the Vision to Transform Ghana into an Information-Rich Knowledge–Based Society and Economy through the Development, Deployment, and Exploitation of ICTs within the Economy and Society. Retrieved on 30th November 2022 from https://nita.gov.gh/theevooc/2017/12/Ghana-ICT4AD-Policy.pdf
United Nations Office on Drugs and Crime (UNODC) (2019). Acting to stop cybercrime. Retrieved on February 9, 2023, from https://www.unodc.org/lpo-brazil/en/frontpage/2018/04/article_-acting-to-stop-cybercrime.html#:~:text=The%20unprecedented%20scope%20of%20cybercrime,of%20cybercrime%20at%20%24%20600%20billion.
United Nations Office on Drugs and Crime (2019). The role of the cybercrime law. Retrieved on 9th March 2023 from https://www.unodc.org/e4j/en/cybercrime/module-3/key-issues/the-role-of-cybercrime-law.html
Wilczek, M. (2020). Cybercrime May Be the World’s Third-Largest Economy by 2021. Retrieved on 1st December 2022 from https://www.darkreading.com/vulnerabilities-threats/cybercrime-may-be-the-world-s-third-largest-economy-by-2021
Wass, S. (2019). Paperless Port System Prompts Import Revenue Growth in Ghana. Retrieved on 5th December 2022 from https://www.gtreview.com/news/africa/paperless-port-system-prompts-import-revenue-growth-in-ghana/
World Economic Forum. Global Risks Reports – 2018, 2019, 2020. Retrieved from www.weforum.org on February 9, 2023.
World Economic Forum (2020). 3 ways government can address cyber security in the post-pandemic world. Retrieved on 9th March 2023 https://www.weforum.org/agenda/2020/06/3-ways-governments-can-address-cyber-threats-cyberattacks-cybersecurity-crime-post-pandemic-covid-19-world/

